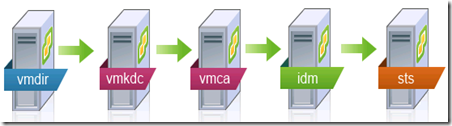
SSO is actually quite complex in the sense that there are quite a few services running under the umbrella of this SSO service.
VMware Directory Service
A directory service is a software system that stores, organizes and provides access to information in a directory. In software engineering, a directory is a map between names and values. It allows the lookup of values given a name, similar to a dictionary.
This description may sound very much the same as one for a relational database, but there are a number of things that distinguish a traditional directory service from a typical relational database. Of course there are exceptions, but in general:
Directory information is read more often than it is written; this makes features related to transactions and rollback less important.
Data can be redundant if it helps performance.
Directory schemas are defined as object classes, attributes, name bindings and knowledge (namespaces)
This description may sound very much the same as one for a relational database, but there are a number of things that distinguish a traditional directory service from a typical relational database. Of course there are exceptions, but in general:
Directory information is read more often than it is written; this makes features related to transactions and rollback less important.
Data can be redundant if it helps performance.
Directory schemas are defined as object classes, attributes, name bindings and knowledge (namespaces)
Active Directory, OpenLDAP, and eDirectory are examples of well-known Directory Services. VMware Directory also has similar functionality to these examples. If you have experience with another LDAP implementation, it will be very valuable to you as you troubleshoot or interact with “vmdir”.
The following table documents some information about the service:
| Ports | TCP 2012 (Control Interface), TCP 11711 (LDAP), TCP 11712 (LDAPS) |
| Process Name | vmdird.exe |
| Data Location (Windows) | C:\ProgramData\VMware\CIS\data\vmdird\data.mdb |
| Installation Location (Windows) | C:\Program Files\VMware\Infrastructure\VMware\CIS\vmdird |
vmdir has a built-in automatic replication engine. This engine will allow various SSO 5.5 instances to maintain consistent information across various SSO nodes. vmdir uses a Multi-Master Replication topology. Multi-Master Replication is a replication model where entries can be written and updated on any of several master replica copies without requiring communication with other master replicas before the write or update is performed.
What this functionality means for SSO 5.5 is that when configuration changes are made on one node, those changes are replicated automatically (every 30 seconds) to every other node in the environment. This is very similar to how Microsoft Active Directory works.
What this functionality means for SSO 5.5 is that when configuration changes are made on one node, those changes are replicated automatically (every 30 seconds) to every other node in the environment. This is very similar to how Microsoft Active Directory works.
VMware Identity Management Service (idm)
The VMware Identity Management Service is in many ways the heart of the SSO 5.5 system. This service handles incoming authentication requests, and routes them to the appropriate directory or identity source.
The following table documents some information about the service:
| Ports | TCP 12721 |
| Process Name | VMwareIdentityMgmtService.exe |
| Data Location (Windows) | C:\ProgramData\VMware\CIS\data\vmware-sso |
| Installation Location (Windows) | C:\Program Files\VMware\Infrastructure\VMware\CIS\vmware-sso |
VMware Secure Token Service (sts)
The Secure Token Service is responsible for issuing security tokens once the user identity is verified. This service runs the Tomcat server which is the closest analog to the original SSO 5.1 configuration.
The Admin Service and Lookup Service which were part of SSO 5.1.0 are still present in SSO 5.5 for legacy compatibility. The VMware Secure Token Service owns these two applications, and presents them in the same fashion as SSO 5.1 did.
Admin Service: https://<FQDN>:7444/sso-adminserver/sdk
Lookup Service: https://<FQDN>:7444/lookupservice/sdk
The following table documents some information about the service:
| Ports | TCP 7444 |
| Process Name | wrapper.exe |
| Data Location (Windows) | C:\ProgramData\VMware\CIS\data\vmware-sso |
| Installation Location (Windows) | C:\Program Files\VMware\Infrastructure\VMware\CIS\vmware-sso |
The sts service currently supports only the WS Trust token specificiation, which is is a WS-* specification that provides extensions to WS-Security, specifically dealing with the issuing, renewing, and validating of security tokens, as well as with ways to establish, assess the presence of, and broker trust relationships between participants in a secure message exchange.
VMware Certificate Service (vmca)
The VMware Certificate Service is an X.509 compliant certificate authority, which supports issuing and revocation of certificates.
The following table documents some information about the service:
| Ports | TCP 2014 |
| Process Name | vmcad.exe |
| Data Location (Windows) | C:\ProgramData\VMware\CIS\data\vmca |
| Installation Location (Windows) | C:\Program Files\VMware\Infrastructure\VMware\CIS\vmcad |
The vmca service requires its own Root certificate. This certificate is generated automatically during the installation of SSO 5.5. The certificate is 2048-bit sha256 self-signed. It will be valid for 10 years from the date of creation.
vTip: Replacing the root vmca certificate is not supported.
vTip: You can view the certificate at C:\ProgramData\VMware\CIS\data\vmca\root.cer
vTip: Replacing the root vmca certificate is not supported.
vTip: You can view the certificate at C:\ProgramData\VMware\CIS\data\vmca\root.cer
VMware Kdc Service (vmkdc)
The VMware Kdc Service is Kerberos KDC capable of issuing tickets for use by the VMware Certificate Service.
The following table documents some information about the service:
| Ports | TCP 88, TCP 2013 |
| Process Name | vmkdcd.exe |
| Data Location (Windows) | C:\ProgramData\VMware\CIS\data\vmkdcd |
| Installation Location (Windows) | C:\Program Files\VMware\Infrastructure\VMware\CIS\vmkdcd |
Starting services
This is the recommended startup order:1. VMware Directory Service
2. VMware Kdc Service
3. VMware Certificate Service
4. VMware Identity Management Service
5. VMware Secure Token Service